
One of the biggest dangers to small business and large government networks alike is phishing. Phishing emails were responsible for nearly a quarter (22%) of all data breaches in 2020 and delivered 94% of malware in 2019.
Both home and business networks are put in danger by phishing emails. Just one wrong click can mean a ransomware infection that causes days of downtime for a company or a theft of your online banking details.
Let’s take a look at what phishing emails are and how you can improve your ability to spot and avoid them.
Understanding Phishing Emails
Phishing emails, also known as phishing scams, are emails designed to trick users into taking a specific action. That action could be anything from clicking over to a fake website and using Amazon login details to login (giving them over to the hacker in the process) or opening a file attachment that releases spyware.
Phishing emails first began in the early days of the internet as those “Nigerian Prince” style emails. Where someone would send a long letter about being a prince, military member, or similar with a request for money that was promised to be paid back.
Today’s phishing emails look a lot different and are much harder to spot from the real thing. They can be spoofed to look exactly like a well-known company, down to the company’s signature and logo.
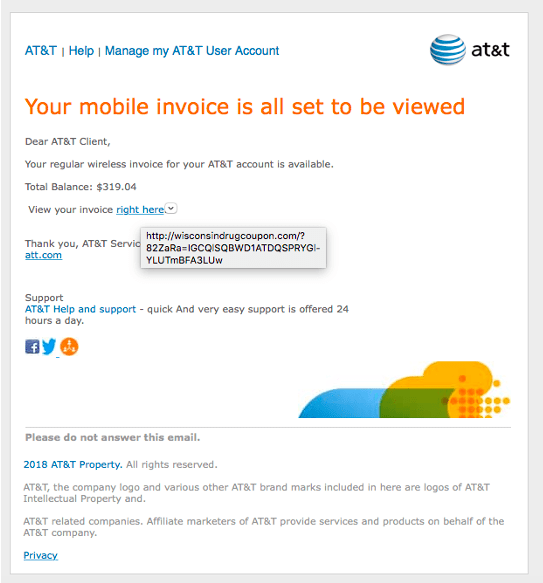
Here’s an example of one designed to look like an AT&T email. Hovering over the link that says “right here” displays a popup that shows the link’s URL isn’t to AT&T at all.
Two Main Dangers in Phishing Emails
The two main dangers contained in phishing emails are file attachments and links.
Certain file attachments can release malware throughout your device as soon as you open it. This includes Word and Excel files that contain macros.
And once one device is infected, malware often is designed to spread through network connections to as many devices or synced cloud accounts as possible.
The most popular type of phishing email tactic, and one that is even more dangerous than an attachment, is a link.
Why is a link more dangerous? Because people tend to trust them more than a file attachment. Also, links to malicious sites can often bypass certain antivirus programs that are looking for malware. A link doesn’t contain malware itself, so it’s often not detected.
Approximately 88% of phishing emails use URLs to malicious sites, rather than file attachments.
Malicious links are also often hidden behind text, buttons, or images.
Types of Common Phishing Emails
- Fake invoices or shipping notices with links
- Fear notices, e.g., “Your account is about to be locked!”
- Notices from “coworkers” with “look at this” and a link
- Fake file sharing emails that spoof services like Dropbox and OneDrive
- Scam purchase order attachment
- Contest winner scams
- Phishing related to the pandemic (fake vaccine or outbreak maps, etc.)
- Government/tax related email scam
- The billing problem “fix your billing settings” attack
- Fake bank account notices
- Holiday-related scams (fake charity requests, holiday schedules, etc.)
Goals of Phishing Attacks?
Phishing emails are the delivery method for any number of scams, attacks, and other nefarious enterprises. You can think of phishing as the trucks that transport multiple goods and food products around the country. The items being transported can vary widely, but in the case of phishing it’s all meant to cause you or your business harm.
Some common phishing goals are:
- Steal money
- Steal login credentials to take over an account
- Get credit card details
- Plant ransomware to extort money
- Steal sensitive information through spyware or a system breach
- Plant other types of malware that can allow a user into a system through a backdoor, or just disrupt your operations
Tips to Avoid Phishing Emails
Hover Over Links
You can quickly reveal the true URL of a text or image link in an email by hovering over the link with your cursor rather than clicking.
Ask Yourself, “Is This Email Expected?”
In today’s climate of cybercrime, you have to take a stance of not automatically trusting all emails in your inbox until they prove you otherwise. Instead, assume any of them could be phishing.
An important question to ask yourself and that can help you stop and stay before reacting to an email is, “Is this email expected?” If not, proceed with extreme caution.
Look for Anything That’s Off
Phishing emails are much more sophisticated these days, making them harder to tell from the real thing. However, some still do have things that are slightly off that give them away.
These can include the use of a non-familiar or foreign word or phrase, or a slight misspelling or grammar error.
Take a Phishing Test to Hone Your Skills
97% of people are unable to recognize a sophisticated phishing email. But you can hone your skills by taking phishing awareness testing, which helps you learn to identify phishing attacks. Make use of an email address validator tool to be sure that only valid emails will end up on your list. You should also be using an email address from 10 Minute Mail to add a layer of security between you and the websites you sign up for.
There are many you can find for free online, here is a phishing test from PhishingBox.
Protect Yourself From Phishing Emails With Help From Two River Computer
Email filtering and web protection go a long way towards protecting your device and network from phishing attacks. Ask us how we can help your Fair haven, NJ home or business network stay protected!
Contact us today for a consultation. Call 732-747-0020 or reach us online.


