
One of the most prevalent types of malware that is in the news often is ransomware. This type of attack is particularly disruptive and can result in a business being at a standstill for days.
Ransomware has a unique interaction with the hacker that you don’t see with other types of malware. This comes in the form of a ransom demand to alleviate the damage that the infection has caused.
The average cost of remediating a ransomware attack is $732,520, and that cost doubles if the ransom is paid.
Because this form of malware is growing, it’s important for small businesses to put cybersecurity safeguards in place to protect themselves.
Here’s How Ransomware Works
Ransomware is a form of malware that will encrypt, or otherwise make unusable, data stored on a computer, server, or in a cloud account.
As soon as the ransomware infects a device, it will begin scrambling all the files so the user can’t access them. This form of malware also spreads quickly, looking for any other devices connected to the same network that it can infect. It can also spread to cloud storage accounts that may be syncing with a device.
There are two main types of ransomware:
- Crypto: Encrypts data, and a decryption key is needed to unscramble it.
- Locker: Doesn’t encrypt data but locks the user out of being able to access it.
Once a computer or server is infected with ransomware, the user will find out in two ways. One is the inability to access data on the device, and the other is an electronic ransom note that will appear on the screen.
The ransom note will make a demand for a “ransom” the user must pay to regain access to their data. It will usually request the ransom in the form of bitcoin (a cryptocurrency) because it’s untraceable. Some ransom notes will even have a countdown timer, warning that the victim has a certain number of hours to comply or the ransom demand will increase.
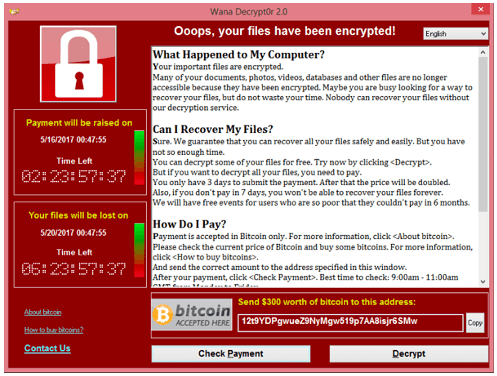
Example of ransomware demand. Photo credit: Wikipedia
When an organization is hit with ransomware, they typically have two options:
- Pay the ransom and hope that the hacker comes through with the decryption key; or
- Have the ransomware professionally removed and restore all their data from a backup
The key to being able to get out of a ransomware attack without having to pay a hacker is having a good backup and disaster recovery system in place.
If you have all your data safely backed up and secure, then the ransomware attacker loses their leverage over you, because you can recover it in another way.
Time is of the essence during a ransomware attack because most organizations can’t operate without having access to their data. For example, a doctor’s office may not have access to any patient records in their system. Making it difficult to properly treat anyone.
A New Twist That Makes Prevention Even More Important
An alarming new twist on ransomware attacks has made them even more dangerous, because even if an organization has a backup, the attacker still demands payment.
This new trend is the demand for payment as extortion to keep the hacker from publicly releasing the data that they’ve been able to access during the attack. This involves the hacker not just releasing code that encrypts or locks users out of files, but also stealing those files themselves.
This type of extortion happened in September of 2020 to University Hospital New Jersey in Newark. The ransomware attackers demanded money in exchange for them not releasing sensitive data online, including patient information. The hospital paid the attackers $670,000.
Should My Small Business Worry About Ransomware?
While municipalities, schools, and hospitals are often the ones covered in news stories when it comes to ransomware, small businesses are actually a main target for these types of attacks.
62% of ransomware attacks happen to small and medium-sized companies. Attacks are also on the rise.
The number of ransomware attacks happening per second has continued to increase:
- 2016: 1 attack every 40 seconds
- 2019: 1 attack every 14 seconds
- 2021 (projected): 1 attack every 11 seconds
Protection from Ransomware
To protect your business from ransomware takes a multi-layered approach that includes multiple safeguards, both for phishing attacks and for network and account intrusions.
These include:
- Patch/update management
- Web filtering
- Email spam/phishing filtering
- Network firewall
- Device antivirus/anti-malware
- Cloud security configurations to prevent ransomware/malware
- Backup and recovery
Pro-Active Support Offers Multiple Layers of Protection from Ransomware & Other Threats
Two River Computer can help your New Jersey business protect your devices from ransomware infections through our Pro-Active Support (PAS) program. It’s one easy plan that offers several strong layers of protection!
Contact us today to learn more. Call 732-747-0020 or reach us online.


